LifeOmic Brand Abuse
Posted September 23, 2022 by Adam Cole ‐ 2 min read
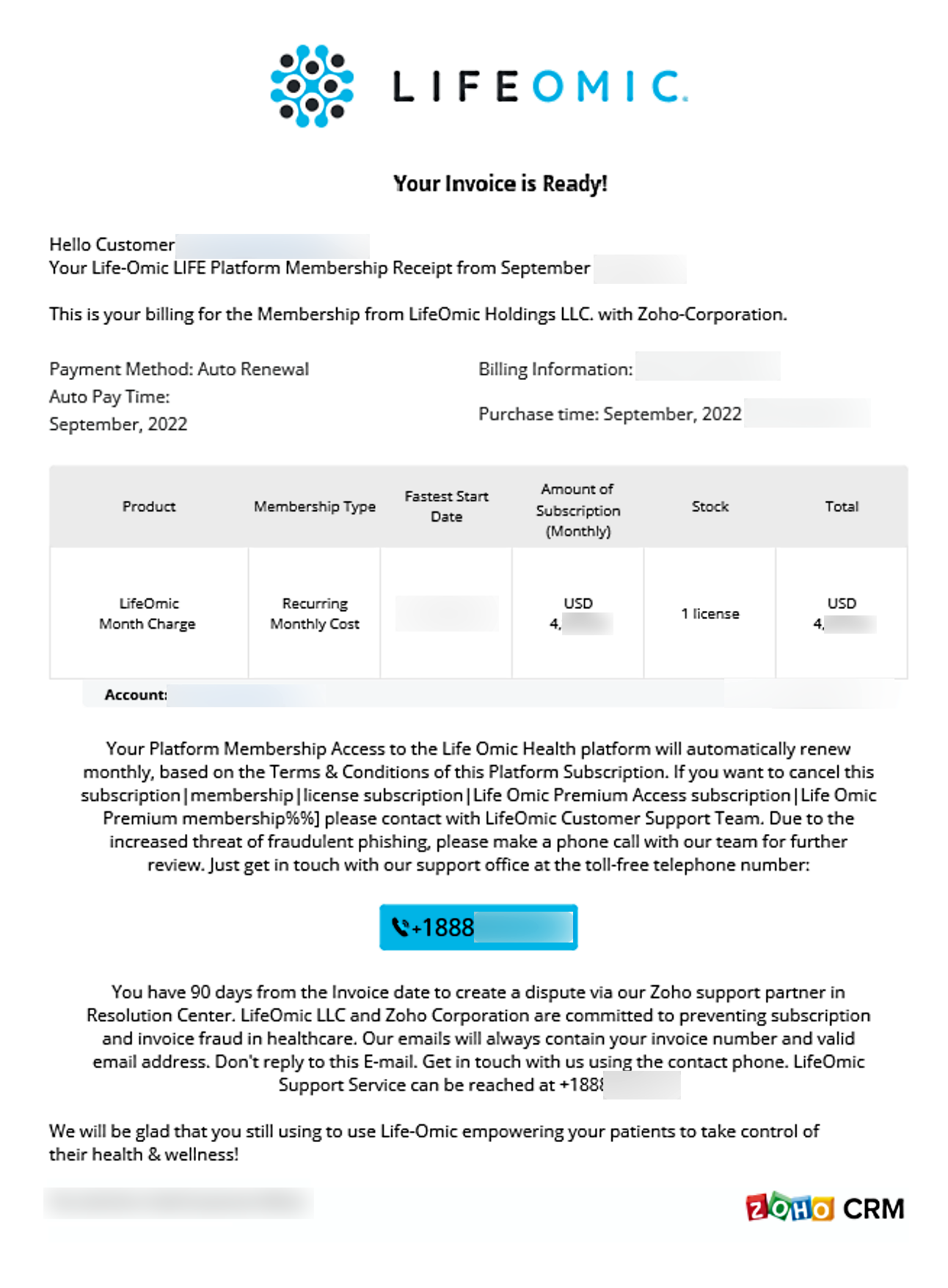
It has come to our attention that LifeOmic’s name has been used in a sophisticated phishing scheme. The phishing message attempts to convince users that LifeOmic has sent them an invoice and, in order to pay the invoice, you must call the number in the email.
As soon as the phishing attempts were reported to us, we opened an internal investigation to ensure this was not an incident involving internal LifeOmic data. Once we confirmed that the target list appeared to be unrelated to LifeOmic and that no internal data was being used by the threat actors, our next steps involved escalating to authorities and the cyber security community. We reached out to the FBI, FCC, CISA, and our industry Information Sharing and Analysis Center, H-ISAC, to report the phishing schemes.
After coordinating with these authorities, it appears that the criminals responsible for these phishing emails deceive victims into installing remote operating software on their machines, steal data and/or money. This is called a “BazarCall” style attack, or “callback phishing”. This is an attack vector that utilizes targeted phishing methodology and a call center. Callback phishing tactics have widely proliferated completely changing the current threat landscape.
We want to point out that LifeOmic will NEVER ask you for payment over the phone or permission to install remote assistance tools on your machine. All of LifeOmic’s apps and software use proprietary, industry-accepted payment tools built directly into the apps. If you have any questions for us, we are always available at the LifeOmic Contact Page.
If you have become a victim of a phishing attempt like this, please report the incident to the FBI. You can file a report at ic3.gov.
A redacted version of this email is below:
If any change to the situation occurs, we will update this blog post.